Cybersecurity isn’t just a buzzword anymore. It’s the frontline defense keeping businesses, governments, and individuals safe from digital threats that evolve every single day. And at the heart of this defense? Ethical hackersthe white-hat warriors who think like attackers but fight for protection.
What is Ethical Hacking?
Ethical hacking is essentially breaking into systemsbut with permission and a purpose. We’re talking about professionals who legally identify vulnerabilities in networks, applications, and infrastructure before the bad guys do.
Think of it this way. If a malicious hacker is a burglar testing every door and window to break in, an ethical hacker is the security consultant you hire to find those weak points first. Same techniques. Opposite intentions.
At Go Hackers Cloud, we’ve designed our ethical hacking training course specifically for beginners who want more than just theory. We’re talking real-world simulations, actual attack scenarios, and hands-on labs that mirror what you’ll face in the field.
Not sure if you’re ready for ethical hacking? Start with our Cyber Security Training for Beginners to build foundational knowledge first.

The ethical hacking certification you earn here isn’t just a certificate. It’s proof you’ve done the work.
Why Ethical Hacking is a High-Demand Career in India
We’ve seen it firsthandcybercrime in India has exploded. Data breaches. Ransomware attacks. Financial fraud. The numbers are staggering, and organizations are scrambling to find skilled professionals.
Here’s what’s happening right now:
Cybersecurity roles in India grew by over 350% in the last three years alone. Companies across BFSI, healthcare, e-commerce, and government sectors are actively hunting for trained ethical hackers. Entry-level positions start at ₹4-6 lakhs annually, and experienced professionals easily cross ₹15-20 lakhs.
But here’s the catch. Most graduates don’t have practical skills.
That’s where our ethical hacking course makes the difference. We’re not just teaching conceptswe’re preparing you for actual security operations centers, penetration testing roles, and vulnerability assessment teams.
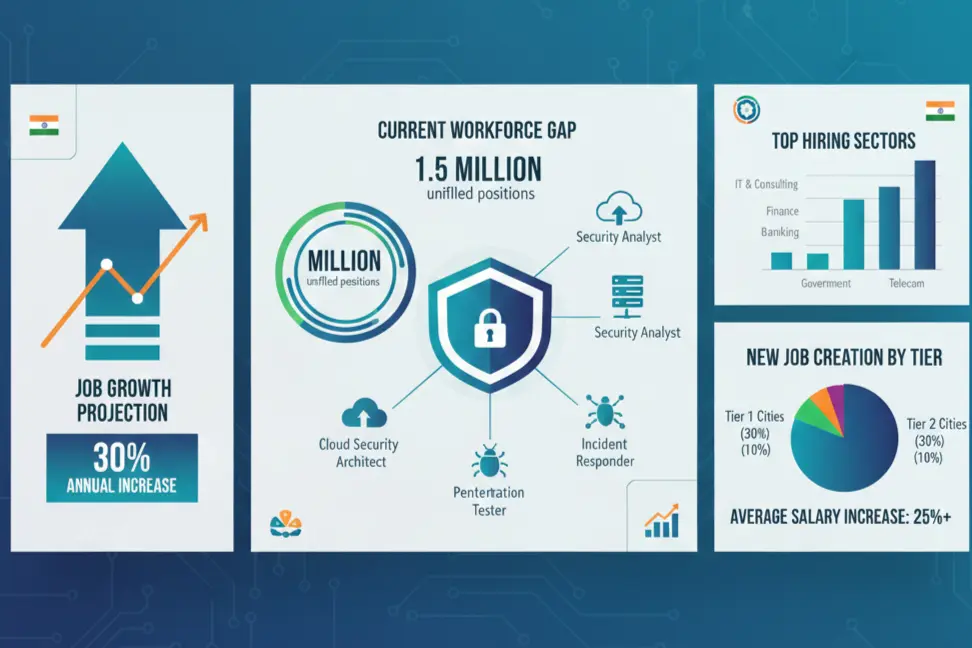
The demand isn’t slowing down. If anything, it’s accelerating.
Explore our complete Cyber Security Training Courses to see how ethical hacking fits into your cybersecurity career journey.
Skills You’ll Learn in Our Ethical Hacking Training Course
Let’s be realno employer cares if you can recite definitions. They want to know: can you actually secure their systems?
Our ethical hacking training course with certification focuses exclusively on practical, job-ready skills.
You’ll master:
Network Security Fundamentals – Understanding TCP/IP, subnetting, and how data actually moves across networks. Not just theoryyou’ll be sniffing packets and analyzing traffic.
Linux Command Line Mastery – Most security tools run on Linux. We’ll get you comfortable navigating, scripting, and troubleshooting like a pro.
Footprinting & Reconnaissance – This is where every attack begins. You’ll learn to gather intelligence on targets using OSINT techniques and automated tools.
Vulnerability Assessment – Identifying weaknesses before exploiting them. We cover everything from outdated software to misconfigurations.
Web Application Security – SQL injection, XSS, CSRFthese aren’t just acronyms. You’ll exploit these vulnerabilities in controlled lab environments.
Wireless Network Attacks – WPA/WPA2 cracking, evil twin attacks, and securing wireless infrastructure.
Password Cracking Techniques – Understanding hash functions, rainbow tables, and brute-force methods.
Social Engineering Basics – Because the weakest link is often human. You’ll learn psychological manipulation tactics used by attackers.
Each module connects directly to real-world scenarios we’ve encountered in actual penetration tests.
We’ve structured the entire ethical hacker course online around one principle: learn by doing.
Tools Covered (Kali Linux, Metasploit, Nmap & More)
Theory is worthless without tools. And tools are useless without practice.
Here’s what you’ll be working with daily:
Kali Linux – This isn’t just another operating system. It’s your entire penetration testing environment preloaded with 600+ security tools. We’ll have you comfortable navigating it within the first week.
Metasploit Framework – The industry standard for exploit development and vulnerability validation. You’ll be launching exploits, generating payloads, and understanding post-exploitation techniques.
Nmap – Network mapping and port scanning. Sounds simple, but mastering Nmap takes real practice. We’ll cover everything from basic scans to advanced firewall evasion.
Burp Suite – Web application testing powerhouse. You’ll be intercepting requests, modifying parameters, and identifying security flaws in real web applications.
Wireshark – Packet analysis tool that lets you see exactly what’s happening on a network. We use this extensively in our labs.
John the Ripper & Hashcat – Password cracking utilities. You’ll understand hash algorithms and brute-force attacks.
Aircrack-ng – Wireless network security testing. We’ll have you cracking WEP and WPA keys in controlled environments.

Every tool gets dedicated lab time. We’re not doing demosyou’re doing the work yourself.
Ethical Hacking Course Curriculum Overview
We’ve built this curriculum based on direct feedback from hiring managers and security teams. They told us exactly what they need. We built it.
Module 1: Introduction to Cybersecurity & Ethical Hacking
Setting the foundation. Understanding the threat landscape, legal boundaries, and ethical responsibilities.
Module 2: Networking Fundamentals for Security Professionals
Deep dive into OSI model, protocols, and network architecture from a security perspective.
Module 3: Linux for Ethical Hackers
Command-line mastery, bash scripting, and system administration essentials.
Module 4: Information Gathering & Reconnaissance
OSINT techniques, DNS enumeration, and footprinting methodologies.
Module 5: Scanning & Enumeration
Port scanning, service detection, and vulnerability identification.
Module 6: System Hacking & Exploitation
Gaining access, privilege escalation, and maintaining persistence.
Module 7: Web Application Security
OWASP Top 10, SQL injection, XSS, and web-specific vulnerabilities.
Module 8: Wireless Network Security
WiFi protocols, WPA2 cracking, and wireless attack vectors.
Module 9: Malware Analysis Fundamentals
Understanding malware behavior, basic reverse engineering, and threat detection.
Module 10: Reporting & Professional Ethics
Documentation, client communication, and maintaining ethical standards.
Our ethical hacking training online delivery means you get flexible scheduling without compromising on quality. Live sessions. Recorded lectures. 24/7 lab access.
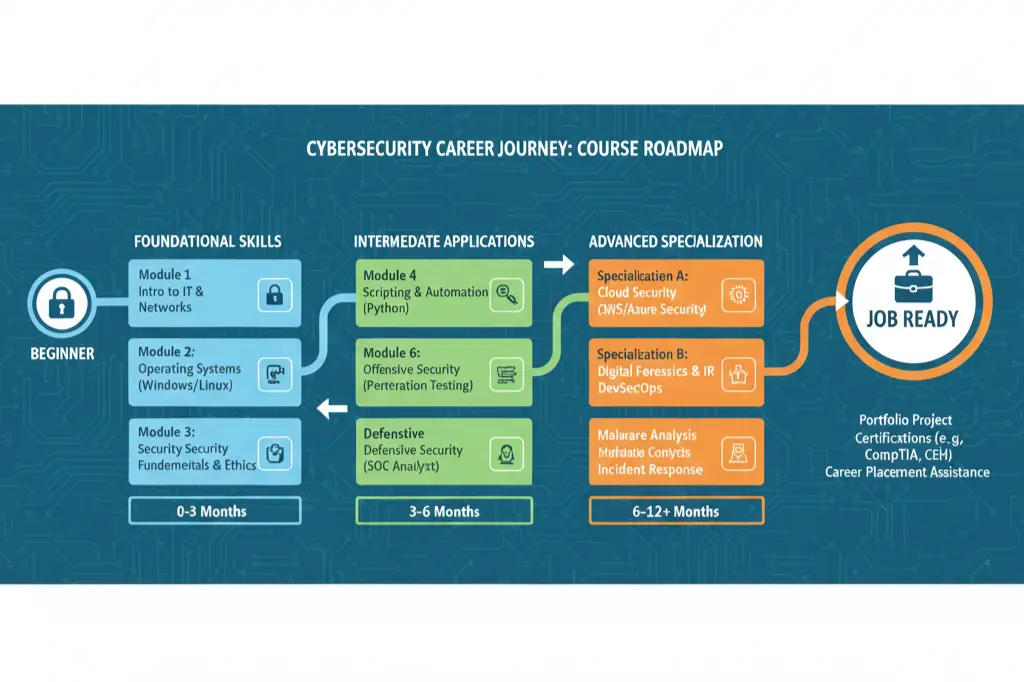
Everything flows logically. Each module builds on the previous one.
Ethical Hacking Certification Included
Completing our program means earning an ethical hacking certification that actually carries weight with employers.
Here’s why our certification matters:
Practical Validation – You’re not just answering multiple-choice questions. You’ve demonstrated actual skills in our labs.
Industry Recognition – Our hiring partners specifically look for candidates with our certification because they know what it represents.
Resume Advantage – In a stack of 100 resumes, having recognized certification gets you noticed. We’ve seen it happen repeatedly.
Interview Confidence – You can back up your certification with real examples from labs you’ve completed.
This certification complements global standards like CEH but focuses specifically on practical, hands-on competency. That’s what makes our ethical hacking training course with certification stand out.
We’ve partnered with companies actively hiring, and they trust our certification process.
Career Opportunities After Ethical Hacking Training
Let’s talk about what happens after you complete the best ethical hacking course in India.
The roles you’ll qualify for include:
Penetration Tester – Actively testing systems and applications for vulnerabilities. This is offensive security work that pays well and stays interesting.
Security Analyst – Monitoring threats, analyzing incidents, and implementing defensive measures.
SOC Analyst – Working in Security Operations Centers, responding to alerts and investigating potential breaches.
Vulnerability Assessment Specialist – Identifying weaknesses across infrastructure and prioritizing remediation.
Network Security Engineer – Designing and implementing secure network architectures.
Incident Response Specialist – Handling security breaches and minimizing damage when attacks occur.
Starting salaries range from ₹4.5-7 lakhs annually. With 2-3 years experience, you’re looking at ₹10-15 lakhs. Senior roles cross ₹20 lakhs easily.
Our ethical hacking course with placement support includes resume building, mock interviews, and direct connections to hiring partners. We’ve placed graduates in companies ranging from startups to major enterprises.

The cybersecurity talent shortage means companies are competing for qualified candidates. You have leverage.
Want to specialize further? Many of our graduates advance to our Penetration Testing Training Course to master advanced exploitation and red team operations.
Why Choose Go Hackers Cloud for Ethical Hacking Training?
We’re not going to claim we’re the only option. But here’s what we’ve built differently:
Expert Instructors from the Field – Our trainers aren’t academics. They’re active security professionals who’ve conducted real penetration tests and incident responses.
Hands-On Lab Infrastructure – Dedicated cloud labs available 24/7. Practice whenever you want. Break things. Learn from mistakes.
Beginner-Friendly Approach – We’ve taught hundreds of students with zero technical background. Our teaching method assumes nothing.
Live + Recorded Sessions – Attend live classes for interaction. Review recordings at your pace. Get the best of both.
Career Support That Actually Works – Resume reviews. Interview preparation. Direct introductions to hiring managers. We’re invested in your success.
Updated Curriculum – Cybersecurity evolves fast. We update content quarterly based on emerging threats and industry feedback.
Community Access – Join our alumni network, participate in CTF competitions, and stay connected with peers and mentors.
We’re not selling courses. We’re building careers.

Visit us at https://gohackerscloud.com/ and see what makes our approach different.
Frequently Asked Questions
Can I learn ethical hacking with zero technical background?
Absolutely. We’ve designed our ethical hacking training course specifically for beginners. We start with fundamentals and gradually build complexity. Most of our successful students came from non-technical backgroundscommerce graduates, mechanical engineers, even artists. What matters is commitment, not prior experience.
How long does the ethical hacking course take to complete?
The core curriculum spans 12-16 weeks with flexible scheduling. If you’re dedicating 10-15 hours weekly, expect 3-4 months. Our self-paced option lets you go faster or slower based on your schedule. Lab access continues for 6 months after course completion.
Will I get job assistance after completing the certification?
Yes. Our ethical hacking course with placement support includes resume building, LinkedIn optimization, mock interviews, and direct introductions to hiring partners. We can’t guarantee jobsthat depends on your performancebut we provide every resource to maximize your chances.
Is this course recognized by employers in India?
Our ethical hacking certification is recognized by 200+ hiring partners across India. Many specifically request candidates trained by us because they trust our practical approach. The certification complements but doesn’t replace global certifications like CEH, OSCP, or CompTIA Security+.
What makes this the best ethical hacking course in India?
Strong claim, but here’s our reasoning: hands-on labs that mirror real scenarios, instructors with active security careers, updated curriculum reflecting current threats, and proven placement support. We measure success by graduate employment rates, not enrollment numbers.
Do you offer both online and classroom training?
Currently, we focus exclusively on ethical hacking training online with live instructor-led sessions. This gives you flexibility without sacrificing interaction. You get recorded sessions, 24/7 lab access, and live doubt-clearing sessions.
What tools and software will I need?
Nothing expensive. A laptop with 8GB RAM and decent internet connection. We provide cloud-based labs with all necessary tools pre-installed. Kali Linux, Metasploit, and other software run in our environmentyou access them through your browser.
Can I get a refund if I don’t like the course?
We offer a 7-day money-back guarantee. Attend the first week, access labs, interact with instructors. If you’re not satisfied, we refund completely. We’re confident you’ll stay.
Start Your Ethical Hacking Journey Today
The cybersecurity skills gap isn’t closingit’s widening. Every day companies struggle to find qualified professionals who can actually protect their systems. Every day, talented people stay stuck in unfulfilling careers because they don’t know where to start.
We’ve trained hundreds of beginners who are now working as penetration testers, security analysts, and ethical hackers. They started exactly where you are right nowcurious, uncertain, but ready to learn.
Our Ethical Hacking Training Course gives you everything: practical skills, industry-standard tools, recognized certification, and career support that extends beyond graduation.
The question isn’t whether cybersecurity is the right field. The question is: are you ready to start?
Enroll in Go Hackers Cloud’s Ethical Hacking Training Course and transform your career in cybersecurity.
👉 Visit https://gohackerscloud.com/ to explore our curriculum, talk to course advisors, and take the first step toward becoming a certified ethical hacker.
Don’t wait for the perfect moment. The industry needs skilled professionals now. Your future in cybersecurity starts today.


