Cyber threats aren’t slowing down. They’re getting smarter, faster, more dangerous. Organizations are scrambling to protect their digital assets, and there’s one role that’s become absolutely critical: the SOC Analyst.
If you’ve ever wondered what it’s like to be on the frontlines of cybersecurity, detecting threats before they become disasters, you’re about to find out. We’re not talking about theory-heavy courses that leave you unprepared. We’re talking about real skills, real tools, and real career opportunities waiting for you through comprehensive cyber security training courses.
At Go Hackers Cloud, we’ve built something different. Our SOC Analyst Training Course transforms complete beginners into confident professionals who can walk into any Security Operations Center and make an immediate impact.
Let’s dive into everything you need to know.
What is a SOC Analyst? Your Role as a Digital Guardian
A SOC Analyst is your organization’s first line of defense against cyber attacks. Period.
Think about it. Every second, thousands of events are happening across a company’s network. Logins. File transfers. API calls. Most are harmless. But buried in that noise? Threats that could cost millions.
That’s where you come in.
We’ve seen SOC Analysts catch ransomware before it encrypted critical files. We’ve watched them identify data exfiltration attempts in progress. These aren’t just jobs—they’re missions that protect people’s data, companies’ reputations, and sometimes even national security.
In our SOC analyst course, you’ll learn to think like both the defender and the attacker. You’ll understand how threats move through networks, how they hide their tracks, and most importantly, how to stop them.
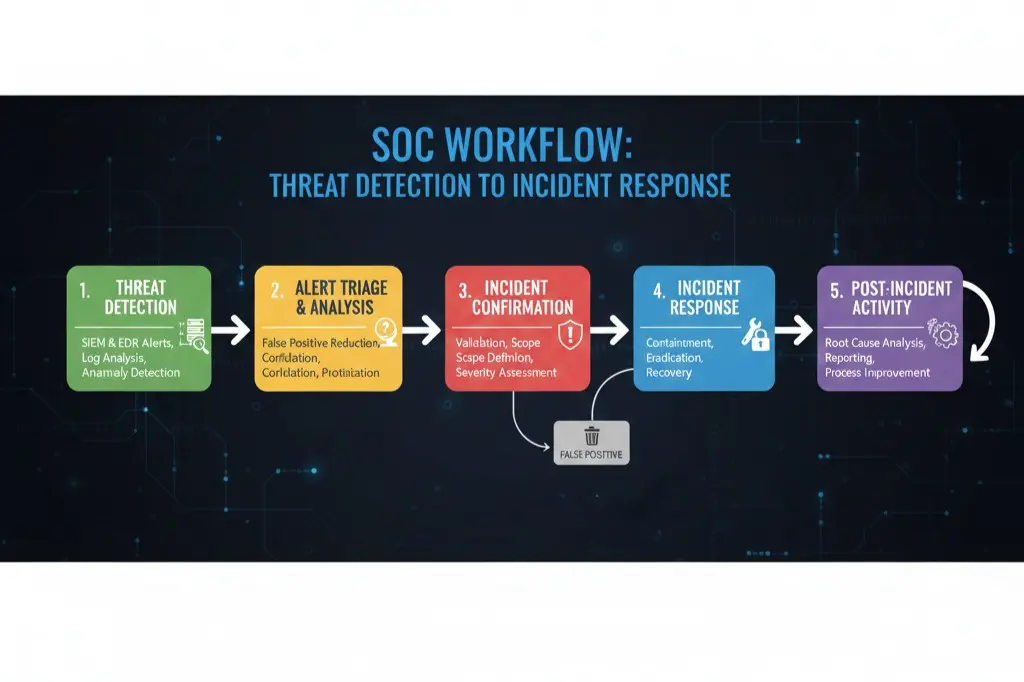
SOC Roles & Responsibilities: What You’ll Actually Do
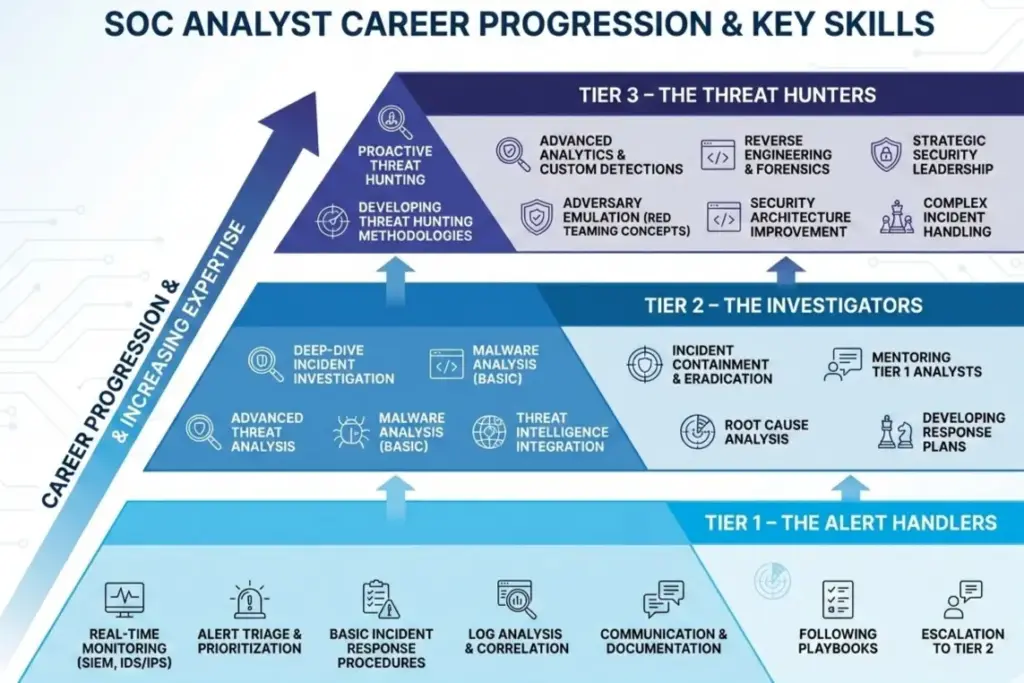
Here’s something most courses won’t tell you. The SOC isn’t just one role. It’s a progression, a career ladder you climb as you gain experience.
Tier 1 – The Alert Handlers
You start here. Monitoring dashboards, triaging alerts, distinguishing false positives from real threats. It might sound basic, but this is where you develop your intuition. Our SOC training, part of our broader cyber security training for beginners pathway, puts you in simulated environments where you’ll handle hundreds of alerts just like you would on day one of your job.
We’ve designed exercises that replicate actual attack patterns—phishing campaigns, brute force attempts, unusual data transfers. You learn to make split-second decisions.
Tier 2 – The Investigators
Now things get interesting. An alert has been escalated to you. You need to dig deeper. Was this malware? What systems did it touch? How did the attacker get in? You’ll use SIEM tools to correlate logs across multiple sources, building a timeline of the attack.
Tier 3 – The Threat Hunters
This is the apex. You’re not waiting for alerts anymore. You’re actively hunting for threats that hide beneath the surface. Advanced persistent threats. Zero-day exploits. The sophisticated stuff that automated tools miss.
SIEM Tools Covered: Master the Platforms Employers Demand
Let’s be honest. You could have a PhD in cybersecurity theory, but if you can’t navigate Splunk or configure an Elastic Stack dashboard, you won’t get hired.
That’s why our SOC analyst training with SIEM tools focuses relentlessly on hands-on practice.
Splunk – The Industry Standard
When we say you’ll learn Splunk, we mean you’ll actually use it. Not watch videos about it. You’ll write SPL queries, create detection rules, build dashboards that would impress any hiring manager. We’ve seen students go from never hearing about Splunk to confidently discussing their capstone project in interviews.
Elastic Stack (ELK) – The Open-Source Powerhouse
Elasticsearch. Logstash. Kibana. Beats. These aren’t just buzzwords. By the end of training, you’ll deploy your own ELK stack, ingest logs from multiple sources, and create visualizations that tell the story of what’s happening in a network.
Microsoft Sentinel – The Cloud Native Solution
Cloud security is exploding. Azure’s security platform isn’t optional knowledge anymore—it’s essential. We’ll show you how to connect cloud resources, leverage AI-powered threat detection, and automate response actions.
Course Curriculum: How We Build Job-Ready Analysts
Our SOC analyst certification program isn’t bloated with unnecessary content. Every module has a purpose, every lab has a real-world parallel. As part of our comprehensive cyber security certification training offerings, this course delivers focused, practical education.
Module 1: Foundation Building
We start with what you need to know. Network protocols. Attack vectors. The cyber threat landscape. We’re not assuming you know this already, but we’re also not wasting your time on irrelevant details.
You’ll understand the MITRE ATT&CK framework—how attackers think, how they move laterally, how they maintain persistence. This framework becomes your mental model for everything that follows.
Module 2: Core SOC Skills
Log analysis. This is where many analysts struggle initially. Windows event logs look like gibberish until you know what to look for. Firewall logs, Linux syslogs, application logs—we teach you to read them like a book.
Threat intelligence isn’t just about downloading IOC feeds. It’s about understanding what makes a threat relevant to your organization. We’ll show you how to prioritize and apply intelligence effectively.
Module 3: SIEM Mastery
This is where theory meets practice. Hard.
You’ll spend weeks inside SIEM platforms, not watching demonstrations but actually configuring them. We give you broken scenarios—misconfigurated rules, missed alerts, overwhelming noise—and you fix them. This is how you learn.
Module 4: The Capstone Experience
Seventy-two hours. A simulated enterprise network. Multiple attack scenarios unfolding simultaneously. This is your final test, and it mirrors the chaos of a real SOC during a security incident.
We’ve had students tell us this capstone was more valuable than any certification exam they’ve taken. Because when you’re done, you know you can handle the job.

Career Opportunities: Where This Path Leads
The SOC analyst course with placement support we offer isn’t just a nice feature. It’s central to what we do.
Here’s what happens after certification:
You become eligible for roles like Security Analyst, Incident Responder, Threat Detection Specialist. Entry-level positions start strong—we’re talking competitive salaries that reflect the critical nature of the work.
But here’s the bigger picture. Cybersecurity has a skills gap. A massive one. Companies are desperate for qualified analysts. With our training and placement support, you’re not just another resume in the pile.
We’ve seen career changers go from completely different industries to landing SOC roles within months of completing the program. That’s not luck. That’s preparation meeting opportunity.
Why Choose Go Hackers Cloud: What Makes Us Different
We’re going to be direct. There are cheaper courses. There are faster courses. But we’ve built something that prioritizes one thing above all: your actual job readiness.
Real Practitioners Teaching Real Skills
Our instructors aren’t just certified trainers reading from slides. They’re active SOC leads, incident responders who dealt with a ransomware attack last week. When they teach you how to investigate an alert, they’re teaching from muscle memory.
Labs That Don’t Hold Your Hand
We give you complex, messy scenarios. Because real networks are complex and messy. You’ll troubleshoot issues, make mistakes, learn from them. This struggle is intentional—it’s how expertise develops.
Placement Support That Goes Beyond Resume Reviews
We’ve built relationships with hiring managers at security firms, MSSPs, enterprise SOC teams. Our support includes interview preparation specific to SOC analyst certification holders, technical assessment practice, and direct introductions where possible.
A Community That Lasts
The cybersecurity community is tighter than you might think. When you join Go Hackers Cloud, you’re not just taking a course—you’re joining a network of professionals who help each other throughout their careers.
Take the First Step Into Cybersecurity
Look, we know there are a thousand things competing for your attention right now. But here’s what we know from years of training analysts: the best time to start was yesterday. The second best time is today.
The cybersecurity field isn’t slowing down. Organizations need skilled SOC Analysts more than ever. The question isn’t whether opportunities exist—they do. The question is whether you’re ready to seize them.
Our SOC Analyst Training Course gives you everything you need. The technical skills. The hands-on experience. The certification that employers recognize. The placement support to help you land that first role.
You could spend months trying to piece together free resources, watching disconnected YouTube videos, never quite sure if you’re learning the right things. Or you could commit to a structured program designed by people who’ve been in the SOC, who know exactly what skills employers are looking for.
Frequently Asked Questions
Do I need any prior experience to start this SOC analyst course?
Not at all. We’ve designed the curriculum to take complete beginners and build them up systematically. If you have basic computer skills and a genuine interest in cybersecurity, you’re ready to start. Some networking knowledge helps, but we cover the essentials early in the program. What matters more than prior experience is your commitment to learning and practice.
How long does it take to complete the SOC training program?
The instructor-led format runs for approximately fourteen to sixteen weeks with scheduled classes and assignments. If you prefer flexibility, our self-paced option gives you access for up to twelve months. Most students complete the program within four to five months when balancing it with full-time work. The certification exam becomes available after you successfully complete the capstone project.
What kind of placement support does Go Hackers Cloud actually provide?
We’re deeply invested in your career success beyond just training. Our placement assistance includes personalized resume optimization for cybersecurity roles, mock technical interviews with feedback from industry professionals, access to our exclusive job portal featuring opportunities from partner organizations, and career mentorship to guide your job search strategy. While we can’t guarantee specific outcomes, our track record speaks to the effectiveness of this support.
Which SIEM tools will I actually get hands-on experience with during training?
You’ll work extensively with three major platforms: Splunk for enterprise log management and security analytics, Elastic Stack for open-source SIEM deployment and management, and Microsoft Sentinel for cloud-native security operations. This isn’t just watching demos—you’ll configure these tools, write detection rules, investigate simulated incidents, and build dashboards. By completion, you’ll have portfolio-worthy projects demonstrating proficiency in all three.
What are the technical requirements to access the training labs?
Our cloud-based lab infrastructure makes this simple. You need a laptop or desktop with a stable internet connection and a modern web browser. That’s it. All SIEM tools, virtual networks, and attack simulation environments are hosted on our platform. No need for expensive hardware or complicated local setups. You can access your lab from anywhere, anytime during your enrollment period.
Is this SOC analyst certification recognized by employers?
Our certification is recognized across the cybersecurity industry because it demonstrates practical, hands-on skills with the actual tools used in SOC environments. Employers value it because graduates can contribute immediately rather than requiring extensive additional training. Many of our hiring partners specifically request candidates with our certification because they know the rigorous, practical nature of the program. The certification, combined with your capstone project portfolio, provides concrete evidence of your capabilities.
Your Cybersecurity Career Starts Here
The path from interested beginner to employed SOC Analyst is clearer than you might think. But clarity doesn’t mean easy. It means focused. It means practical. It means training that mirrors the actual job you want.
We’ve spent years refining this program, incorporating feedback from hiring managers, updating content as new threats emerge, ensuring that every hour you invest translates directly into job readiness.
Cybersecurity isn’t going to become less important. The threats aren’t going to become less sophisticated. Organizations will continue desperately seeking skilled analysts who can protect their assets.
The only question is: will you be ready when those opportunities come calling?
Stop waiting for the perfect moment. The perfect moment is the one where you decide to start. Where you commit to building real skills with real tools under real guidance.
Ready to transform from curious beginner to confident SOC professional?
Visit https://gohackerscloud.com/ and discover how our comprehensive training program can launch your cybersecurity career. View the complete curriculum, explore student success stories, and see why security professionals choose our hands-on approach.
Limited enrollment ensures personalized attention and optimal learning outcomes. The next cohort is forming now.
Secure your future in cybersecurity.
Start your SOC analyst journey with Go Hackers Cloud today.


